
“How to move from security concerns to security empowered”
It’s the new reality for business: the question enterprises are now asking about cloud is “How” not “If.” With features like rapid elasticity, consumption-based pricing, and access to affordable machine learning capabilities, the opportunities presented by cloud technologies are too great to ignore. Security concerns remain one of the few barriers to enterprise cloud adoption, and at Reveal Risk we’ve adopted a common-sense approach that helps navigate the complexity of enterprise cloud security and accelerate implementation.
With this short guide you’ll get some key requirements for an enterprise cloud security program and a framework you can use to move confidently and quickly towards a secure cloud future.

Landscape
There are two critical components to understand about the cloud security landscape in order to effectively manage security risks:
- Your options in the marketplace (Which we will cover here)
- What matters most to you – A solid understanding of your critical business risks (Curious? Contact us at info@revealrisk.com to learn about how we can help with that too!)
The cloud marketplace is made up of thousands of providers and offerings. Traditional models for Infrastructure, platform, and software as a service (IaaS, PaaS, and SaaS) have been challenged and expanded by Identity as a service (IDaaS), Business Process as a service (BPaaS) Artificial Intelligence as a Service (AIaaS) and nearly anything else as a service (XaaS). Enterprises must often choose between multiple similar providers, creating a complex patchwork of gaps and redundancies. Further complicating enterprise cloud management is the rapid pace of change: hundreds of startups, acquisitions, and failures every year require enterprises to constantly re-evaluate existing capabilities as well as acquire new ones
The landscape is also challenging traditional business expectations. Cloud service providers are often unwilling to negotiate contract terms, even in cases where there is an existing relationship with the provider for other enterprise services. The subscription model of the cloud brings a new wave of ownership and data access risks that traditional security models didn’t need to address. We also can’t forget that cloud services have changed the expectations of the workforce, increasing use of personally owned devices to access company data and services, further challenging the traditional security model.
The reality for 21st business is collaboration. Partnership and co-development are vital, and businesses increasingly turn to cloud services to enable these collaborations. Unfortunately, many enterprises look to manage cloud risk by carefully curating approved providers, and collaborations and partnerships eventually force many enterprises to accept relationships with other providers using a complex system of exceptions and usage limits. In an era where time-to-market and agility matter, an effective security plan can’t limit the enterprise to approved providers. You can’t control the technology decision of your partners. At the same time, market dynamics are such that you may be partners today, competitors tomorrow so you also can’t rely on partnership language and good faith to secure your enterprise.
The Framework
From our brief landscape discussion, we can distill a few simple requirements for a security framework:
- Flexible – accommodate IaaS, SaaS, etc. and allow for updates as things change
- Fast – get a recommendation quickly, don’t waste resources on long forms
- Service-driven – can’t rely on getting providers to agree to standard terms
- Data-centric – might not own the network, the device, or even the provider contract
- Business-led – needs to meet the needs of the business, both near- and long-term
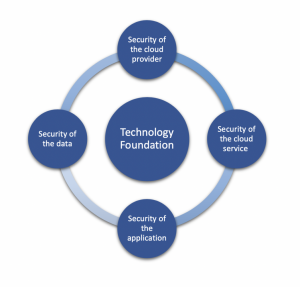
Enterprises can approach the framework question from multiple starting points: the Cloud Security Alliance, Cybersecurity Framework, ISO 27001, COBIT, FISMA, and dozens of other organizations provide guidance, and many companies have gone forward with one of these or a framework of their own in an effort to manage this complex challenge. At Reveal Risk, we start from a simple four-process approach, supported by a technology foundation, that can be adapted to a wide range of organizations:
Security of the Cloud Provider
We start with the security of the cloud provider itself. First and foremost, this is an understanding of the business posture of the provider: financial solvency,
reputation, business practices, pending litigation, etc. While this is usually part
of large cloud contracts, it’s easy to overlook when a regional leader swipes a corporate credit card for an impulse SaaS purchase. The risk to the organization can be considerable, especially considering predatory licensing terms, intellectual property rights, data residency, and brand association.
In addition to the business posture, you may want to consider acquisition risk, physical security of their datacenters, time in business, and how the organization has dealt with negative publicity, if any. Once a deal is struck, enterprises will want to monitor for meaningful changes over the course of the contract.
Security of the Cloud Service
The cloud service offered by the provider may be their sole offering, or one of many that a provider offers. Our experience has shown that even sole-product vendors usually have different terms and configuration options available for different tiers of customers. It’s important for enterprises to understand the guardrails and hardening options available for their specific offering because misconfiguration is the leading cause of cloud security breaches1. This process also helps identify fourth parties and their relevance to your organizational risk posture.
Working closely with your internal team, the security of the service is a joint, ongoing effort. Both the enterprise and the provider have only partial visibility and it’s important to have a good working relationship to address issues and any potential security concerns. Logging and monitoring need to be addressed clearly so responsibilities are understood on both sides of the contract and are executed properly while in operations.
Security of the Application
The approach to security for the application has the most variability based on the type of cloud offering being addressed. For offerings where the application is essentially the service (such as SaaS), application scanning and penetration testing are likely the responsibility of the provider, along with patching and upgrades. Enterprises need to push for the level of information that they need to make informed decisions about their risk.
You have more responsibility, but also more control over applications where your internal developers are part of the capability delivery. Cloud hosted applications need to be checked for common flaws during development and prior to deployment. Regular penetration tests expose logic flaws and configuration issues before they become security incidents. Patching or upgrades need to be thoughtfully designed so that changes can be made quickly when needed.
Security of the Data
Ultimately, the organization needs to protect its data regardless of it being in the cloud or not. Fortunately, many cloud providers automate some of the heavy lifting in terms of key management, encryption, and monitoring.
It’s important for enterprises to understand the use case for a cloud offering before putting sensitive data at risk. Combined with a data classification scheme, the use case can help quickly identify a high or low risk provider. Another important check is whether the provider supports your existing identity and access management structure. If the provider respects the access controls you’ve already established, it goes a long way to reducing your risk.
Logging and monitoring is your last line of defense for data security. If you can pull the logs you can piece together what happened after the fact. If you have a data loss prevention strategy (not just a DLP tool) making sure your cloud services support it as much as possible will dramatically improve your risk posture as well.
Supporting Technology Foundation
The supporting technology that underlies the four processes is important for achieving scale, sustainability, and consistency across your cloud portfolio. Multiple options exist, and each organization will have a different approach that best aligns with their business risk tolerance. The technology pieces can also help achieve speed and cost savings, depending on the circumstances.
Most enterprises consume cloud services at multiple levels, and it’s not uncommon to have different models by business areas or geographies. A solid technical foundation will help create a consistent enterprise view of cloud risk, as well as provide integration to core enterprise security capabilities such as incident management, identity, data protection, and governance.
Conclusion
The cloud security landscape is filled with opportunity. Using the framework outlined here, security doesn’t have to be the last roadblock on the journey to the cloud:
- It’s flexible, not tied to a specific type of cloud offering
- It’s fast, designed to help find and focus on what’s most important to you
- It’s service–driven, focused on what you can do not on getting them to change things
- It’s data–centric, no device or network requirements
- It’s business–led, driving to outcomes not technologies
If you’d like to learn more about how using the framework can accelerate your cloud security journey, contact us at info@revealrisk.com today!
Bonus item
The most common question I get is “How do you make it fast?” The easiest answer: make it risk-based! Find out what matters most to your organization and develop a small set of questions that will tell you quickly if this cloud offering is one to spend time on. Be intentional about where you focus your security lens, and where you enable the organization to move quickly with acceptable risk.